Achieve always-on compliance & cyber resilience, without the overhead
Cut compliance time, costs & complexity – all at once
Centralized, automated & scalable IT compliance in 3 steps
Why Diligent stands out in IT compliance
Purpose-built to streamline compliance and mitigate risk
Always-on compliance monitoring
Spot and fix compliance issues in real-time such as user access violations and segregation of duties - before they become risks.
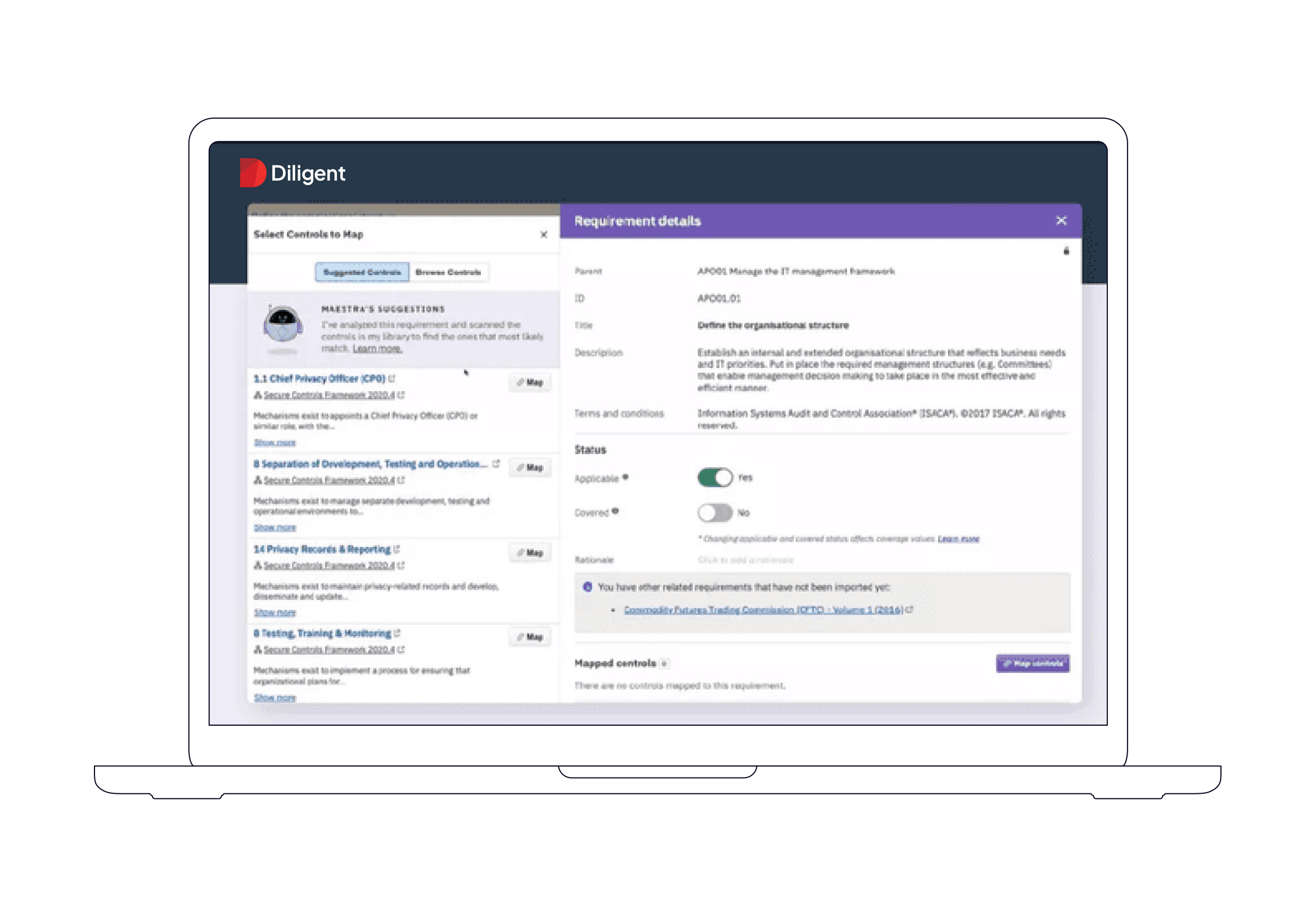
AI control suggestions and generation
Multi-framework scalability
Board-ready, customizable dashboards
Cut compliance time from weeks to hours
See how Diligent automates workflows, streamlines evidence collection, and keeps you always audit-ready — without the overhead.
What success looks like with Diligent IT Compliance
Frequently Asked Questions
Explore how Diligent empowers organizations to meet complex compliance demands.
How does Diligent support FedRAMP compliance for federal contractors?
Diligent offers a FedRAMP-authorized platform that centralizes compliance management and automates evidence collection, ensuring alignment with federal IT security standards.
What frameworks are supported by the Diligent IT Compliance solution?
What is the benefit of the Regology partnership?
Make your IT compliance program work smarter, today
Loading form...
Discover how Diligent’s IT Compliance Solution streamlines workflows, automates evidence collection, and helps you stay ahead of evolving regulations — saving time and minimizing risk.






















