U.S. disclosure requirements around cyber security are still vague, nuanced, and evolving. The SEC recently made updates to its February 2018 interpretive guidance, which outlined its expectations for cybersecurity disclosures. In what is likely a precursor to formal regulations, the SEC focused on a few key areas:
For a quick snapshot of today's cyber disclosure landscape, we sat down with Ron Schneider, Director of Corporate Governance Services for Donnelley Financial Solutions, to understand any disclosure trends stemming from the latest proxy season.
Prior to the financial crisis (which was now one decade ago), company proxy discussions of board oversight of risk were often fairly generic or boilerplate, which left investors unsure whether the company had rigorous and effective processes in place or not.
Since then, there has been increased awareness and discussion around a growing array of risks to companies, to their operations, and to shareholder value. Increasingly, the discussion includes cyber risk and climate change risk. In turn, we are seeing companies discuss these topics within their overall proxy discussion of board oversight of risk; in particular, companies are discussing their processes and structures for reviewing cyber and data security risks, and it has resulted in risk discussions that are clearer and more credible than before.
[blockquote source="Ron Schneider, Donnelley Financial Solutions"]When an investor is considering purchasing a stock, they look at both the upside (which includes the company's strategies, leadership teams, and growth prospects) and the potential downside (which includes various risks to the enterprise and their perception of the company's handle on these). So credible discussion of cyber risk and other risk oversight processes are important from a valuation as well as operational standpoint.[/blockquote]
In part because they have long been top targets for hackers, most of the major financial firms do a good job explaining their processes.
Bank of America, which has an excellent proxy statement in many respects, does an effective job discussing this topic and recent enhancements in a section titled "Cybersecurity and Information Security Risk Oversight", which is located within the overall discussion of Board Oversight of Risk on pages 27-28. [Below is just a snippet from the 2018 Bank of America proxy]:
[blockquote source="Bank of America, 2018 Proxy, Board Oversight of Risk section"]...The
Board and Enterprise Risk Committees receive presentations throughout the year on cybersecurity and information security topics. Our Enterprise Risk Committee also annually reviews and approves our Global Information Security Program and our Information Security Policy. In 2016, we updated our Enterprise Risk Committee's charter to make explicit the Committee's responsibility for reviewing cybersecurity and information security as well as steps taken by management to understand and mitigate such risks. At least twice each year, the Board discusses cybersecurity and information security risks with the Chief Operations and Technology Officer and the Chief Information Security Officer. Our Board received quarterly updates on cybersecurity and information security risk in 2017...[/blockquote] See also Verizon Communications, whose 2018 proxy has a section titled "What about data privacy and cybersecurity risk?" (page 19), which is within the larger Risk Oversight section.

I will characterize these and similar thoughtful risk discussions by other companies as proactive disclosures, but clearly only each company knows the frequency and intensity of the attempted data breaches they successfully defend against on a regular basis.
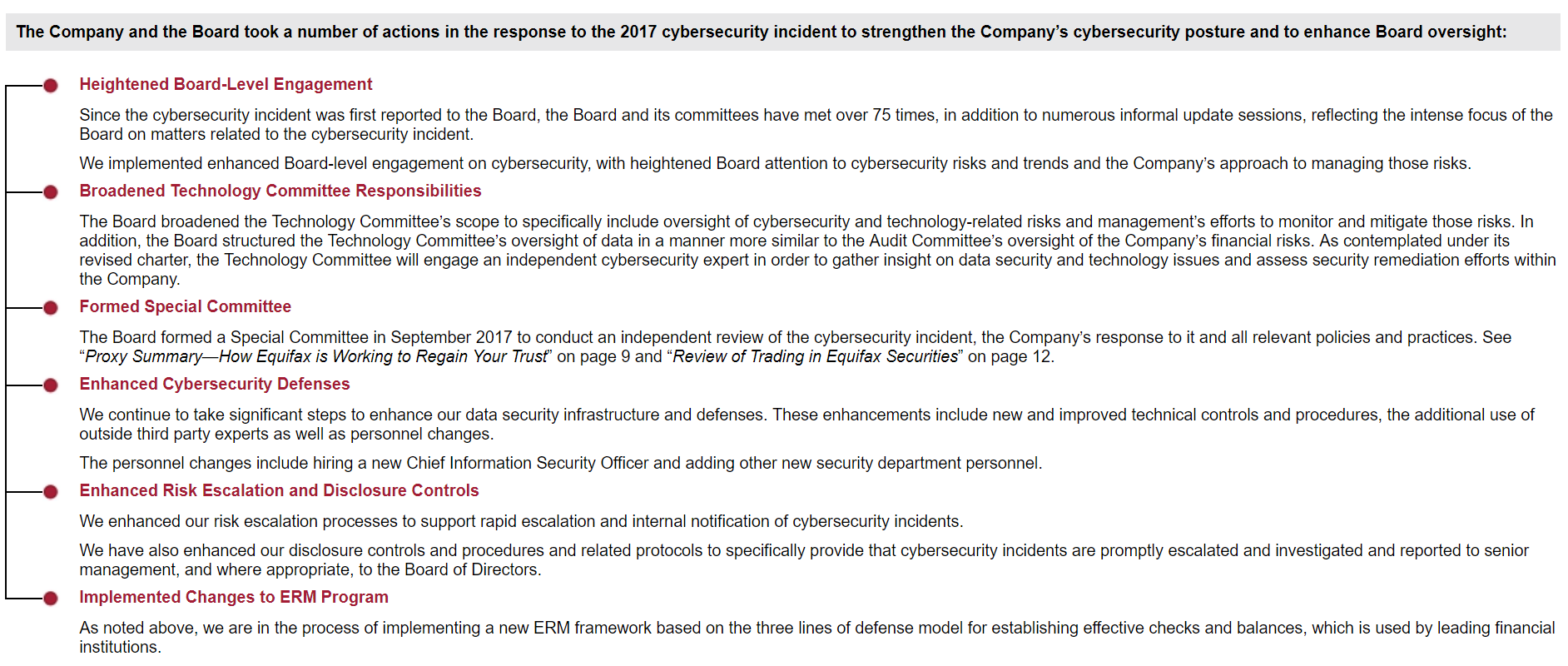
After a major breach becomes public, there is an urgent need to restore confidence. Equifax, in its 2018 proxy statement, spends considerable time discussing the company's response, which included management and board changes, process changes, and even executive compensation implications. See the three-page cover letter from the non-executive chairman of the board, on pages 8-11 of the proxy summary; also see the governance section of their proxy with a section titled '''2017 Cybersecurity Incident and Board Oversight''' (pages 25-27). [Again, here's just a snapshot that links to the full proxy]Equifax, 2018 Proxy Statement (See page 25-27)[/caption]

As more and more citizens, customers, and shareholders become affected by identity theft--and with concerns about outside influence over our country's electoral process--these issues strike home, and it is understandable that this topic will continue to rise in importance with many investors and other stakeholders. In turn, companies will continue to improve both their processes and their discussion of these processes. As investor expectations continue to rise--and as the level and quality of company disclosures continues to improve--there likely will continue to be a ratcheting up process in this regard.
- Companies are expected to disclose material cybersecurity risks and incidents to shareholders, whether they've been the target of a cyberattack or not.
- Companies must have appropriate processes and procedures in place to identify, mitigate, and communicate these risks and incidents as they arise.
- Board directors and executives must avoid any trading of a public company's securities while in possession of material non-public information relating to a cybersecurity incident.
For a quick snapshot of today's cyber disclosure landscape, we sat down with Ron Schneider, Director of Corporate Governance Services for Donnelley Financial Solutions, to understand any disclosure trends stemming from the latest proxy season.
Q: In the wake of a data breach, the board's best defense (from a liability perspective) is to demonstrate that it had a process in place for overseeing cyber risk. Are we seeing any proactive disclosure in the proxy statement around a company's cyber risk oversight process? Why or why not?
Ron Schneider: I will defer to others on the topic of legal and financial liability stemming from a data breach. What may be of equal or even greater significance, is whether the company retains or loses the confidence of current and potential investors, customers, employees, and other stakeholders--this can have a greater impact on the company's share value and future prospects than a fine or judgement.Prior to the financial crisis (which was now one decade ago), company proxy discussions of board oversight of risk were often fairly generic or boilerplate, which left investors unsure whether the company had rigorous and effective processes in place or not.
Since then, there has been increased awareness and discussion around a growing array of risks to companies, to their operations, and to shareholder value. Increasingly, the discussion includes cyber risk and climate change risk. In turn, we are seeing companies discuss these topics within their overall proxy discussion of board oversight of risk; in particular, companies are discussing their processes and structures for reviewing cyber and data security risks, and it has resulted in risk discussions that are clearer and more credible than before.
[blockquote source="Ron Schneider, Donnelley Financial Solutions"]When an investor is considering purchasing a stock, they look at both the upside (which includes the company's strategies, leadership teams, and growth prospects) and the potential downside (which includes various risks to the enterprise and their perception of the company's handle on these). So credible discussion of cyber risk and other risk oversight processes are important from a valuation as well as operational standpoint.[/blockquote]
Q: Any best practices you would share with boards that are looking to improve disclosure around their cyber oversight process? Any proxy examples to share?
RS: As with other proxy disclosure topics, which investors increasingly focus on, companies are viewed not in isolation, but rather relative to both (a) perceived governance leaders and (b) the peer companies these investors also own. As many companies increasingly improve the clarity and credibility of these disclosures, "standing still" becomes less of an option.In part because they have long been top targets for hackers, most of the major financial firms do a good job explaining their processes.
Bank of America, which has an excellent proxy statement in many respects, does an effective job discussing this topic and recent enhancements in a section titled "Cybersecurity and Information Security Risk Oversight", which is located within the overall discussion of Board Oversight of Risk on pages 27-28. [Below is just a snippet from the 2018 Bank of America proxy]:
[blockquote source="Bank of America, 2018 Proxy, Board Oversight of Risk section"]...The
Board and Enterprise Risk Committees receive presentations throughout the year on cybersecurity and information security topics. Our Enterprise Risk Committee also annually reviews and approves our Global Information Security Program and our Information Security Policy. In 2016, we updated our Enterprise Risk Committee's charter to make explicit the Committee's responsibility for reviewing cybersecurity and information security as well as steps taken by management to understand and mitigate such risks. At least twice each year, the Board discusses cybersecurity and information security risks with the Chief Operations and Technology Officer and the Chief Information Security Officer. Our Board received quarterly updates on cybersecurity and information security risk in 2017...[/blockquote] See also Verizon Communications, whose 2018 proxy has a section titled "What about data privacy and cybersecurity risk?" (page 19), which is within the larger Risk Oversight section.

I will characterize these and similar thoughtful risk discussions by other companies as proactive disclosures, but clearly only each company knows the frequency and intensity of the attempted data breaches they successfully defend against on a regular basis.
After a major breach becomes public, there is an urgent need to restore confidence. Equifax, in its 2018 proxy statement, spends considerable time discussing the company's response, which included management and board changes, process changes, and even executive compensation implications. See the three-page cover letter from the non-executive chairman of the board, on pages 8-11 of the proxy summary; also see the governance section of their proxy with a section titled '''2017 Cybersecurity Incident and Board Oversight''' (pages 25-27). [Again, here's just a snapshot that links to the full proxy]Equifax, 2018 Proxy Statement (See page 25-27)[/caption]

As more and more citizens, customers, and shareholders become affected by identity theft--and with concerns about outside influence over our country's electoral process--these issues strike home, and it is understandable that this topic will continue to rise in importance with many investors and other stakeholders. In turn, companies will continue to improve both their processes and their discussion of these processes. As investor expectations continue to rise--and as the level and quality of company disclosures continues to improve--there likely will continue to be a ratcheting up process in this regard.