In the early weeks of COVID-19, the priority was speed. With only a few days notice, organizations had to enable their entire workforce to work from home. For many companies, it was a mad dash to virtual platforms'or at least, a rapid expansion of the technology that was already in place.
Fast-forward to today, and many companies have nearly completed this initial transition. Employees are now connected. Meeting formats have been adapted. New rules of engagement have been established. Yet, beneath this "new normal" is a world of security risks that companies have not yet accounted for.
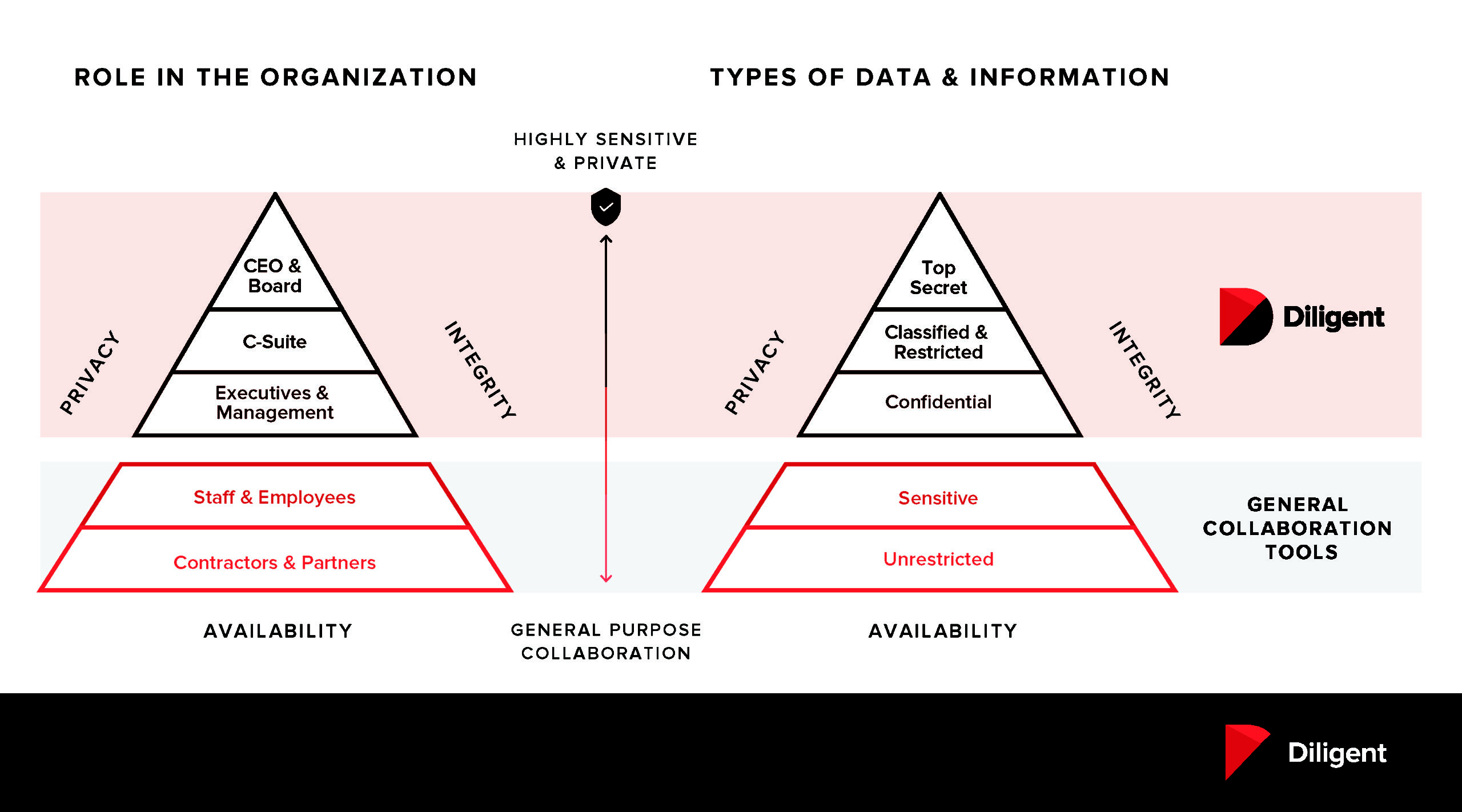
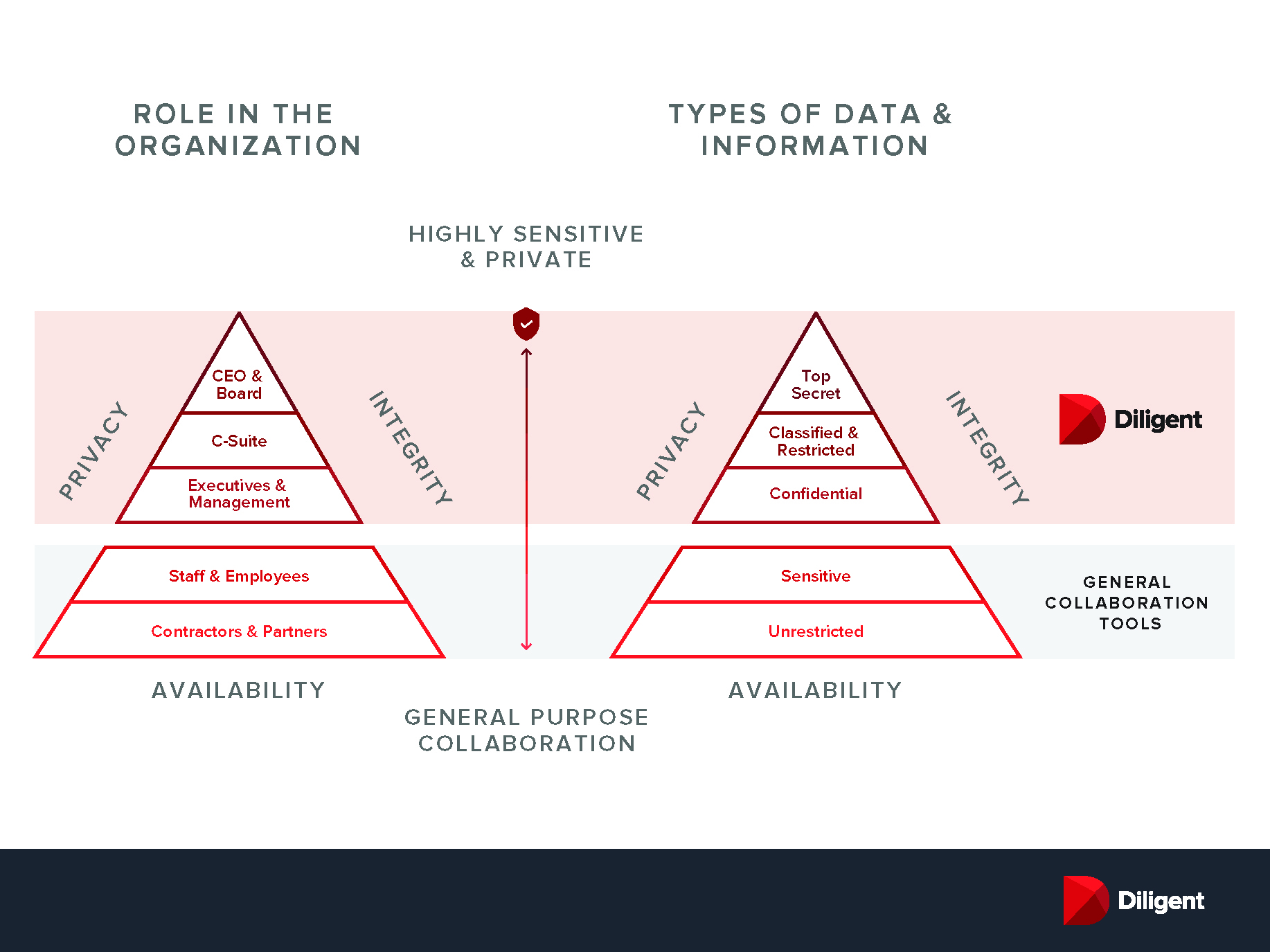
In this new virtual landscape, you're only as secure as your lowest common denominator. Boards, executives and legal teams operate at an information tier that requires a heightened level or privacy and security'one that general collaboration tools cannot provide.
Acknowledging the Risks of Your Virtual Ecosystem
The bad guys have not gone away. Quite the opposite, hackers and other cybercriminals are thriving in a world of immature tools and unsecure workflows. We've seen a surge in Coronavirus-themed phishing, ransomware and DDoS attacks. Popular video-conferencing platforms like Zoom are coming under attack for flaws in their security and data-privacy standards, extending an open invitation to cybercriminals who have something to gain. "Zoom-bombing" may be entertaining when it happens during a virtual happy hour, but shouldn't your organization's most sensitive meetings be better protected?
In the boardroom, governance teams are celebrating the transition to virtual board meetings, yet they're not accounting for all the risks. Video-conference links drift around in unsecure channels like email, where they can be intercepted or accidentally forwarded. Sensitive information is being passed between boards and management teams; yet, organizations have not provided secure channels for these discussions to take place.
In many cases, companies have turned to general-purpose communication tools like Slack, Box or GSuite to provide immediate access and broad connectivity. These tools offer great convenience, but are rarely up to the high privacy and security standards of boards and leadership teams. With open APIs, third parties can have access to organizational data through these platforms. Each external touchpoint or IT support person represents a potential weak link in the chain.
There is an old poker rule that says "If you don't know who the mark at the table is, it's probably you." Similarly, if you're unaware of weak spots in your security, then you're more likely to be the one targeted.
Components of Secure Collaboration
What does a more secure virtual ecosystem look like? It has a few important components:1. Encryption
Encryption capabilities are essential for transmitting secure data and documents. Why? Because sensitive data in transit is increasingly more vulnerable to phishing attacks, password hacks and other potential breaches. Encryption translates "plain text" data into a cryptographic key or a string of characters to protect information in transit. Board members, executives, legal and security teams should have access to encrypted tools like Diligent Messenger (for secure one-to-one or group messaging), Diligent Secure File Sharing (for document share), and Diligent Boards (for secure board communication and meeting management). With multiple levels of encryption, Diligent tools actually encrypt and decrypt data several times while information is in transit providing an even higher standard of security than other similar tools. When using cloud-based video platforms like Zoom or Microsoft Teams, meeting links should be shared only on encrypted platforms to mitigate risk of them falling into the wrong hands.2. Privacy Shielding & User Permissioning
The ability to set user permissions is critical to protecting sensitive information. Yet, additional nuances must be considered at the board and senior leadership levels: (1) Executives and board members need the ability to shield information from system administrators to ensure classified information remains truly classified. They should also be able to extend special permissions to the general counsel or other privileged parties when necessary. (2) User permissions must work just as securely with external third parties (e.g., lawyers, auditors, consultants). The Diligent tools listed above not only support these actions, but they integrate with one another.3. Compliance
Are your new virtual workflows GDPR compliant? Do they follow HIPPA guidelines for protecting employee medical data? Organizations must ensure that the rapid transition to working from home hasn't compromised compliance in critical areas. Platform security must meet regulatory requirements for data processing and transmitting, and compliance often requires both encryption and system integrations.4. Risk & Legal Controls
Mitigating legal risk and discoverability are inherent in any secure collaboration solution. Through these tools, legal counsels should have the ability to either retain or destruct sensitive conversations, documents, and notetaking when necessary. With tools like Diligent Boards and Messenger, messages and notes can be set to expire after a designated period of time set by the general counsel, corporate secretary or CISO. Organizations also need the ability to wipe clean lost devices of all sensitive data. Diligent supports this functionality.5. Seamless User Experience:
Secure tools must mirror the workflows of today's boards and leadership teams. Otherwise, we've made little progress towards a better solution. Secure messaging platforms should feel as seamless as email or text messaging. Minute-taking, voting, and compliance reporting should all integrate with the board's management software. Permissioned users should be able to collaborate in real-time. Diligent's secure collaboration tools support all these features. Organizations mustn't underestimate the importance of integration and user experience when it comes to building secure communication workflows.What is the best way forward? As with Maslow's hierarchy of needs, basic security protections must be prioritized as they represent the largest and most immediate risks in this new virtual world. Yet, the path to securing workflows across the organization doesn't have to be long or tedious. Tools like Diligent can be deployed in a matter of days to connect your board, your executives and your most sensitive information'all in one central, secure workflow. More than ever, a dedicated communication channel is needed at today's most senior leadership levels. The dangers of email have become too great.
The path to a more secure future of work is part of a much larger transformation—one that requires organizations to remain nimble and forward-looking. COVID-19 represents a great obstacle to overcome. Those who recognize the opportunity will find themselves stronger on the other side.