Not only is the prevalence of outsourcing growing, but as the business landscape becomes more complex and globally interconnected, organizations are working with increasing numbers of third parties — meaning the risks companies face from their outsourced operations are growing, too, and with it the need for third-party risk management (TPRM).
35% of directors surveyed in PwC’s 2025 Global Digital Trust Insights survey said they were concerned about third-party data breaches, ranking it among the top three cyber threats. This is particularly true when organizations lack a robust governance framework or at times of crisis or volatility, which is becoming more common in today’s operating environment.
This is why third-party risk management is becoming more commonplace and more vital. Particularly for companies in regulated sectors, managing risk in third-party relationships is non-negotiable and a growing focus for boards and stakeholders.
While it may be growing in popularity, third-party risk management is still an underused strategy for many businesses. This creates a potential — and precarious — blind spot.
Quick third-party risk management summary
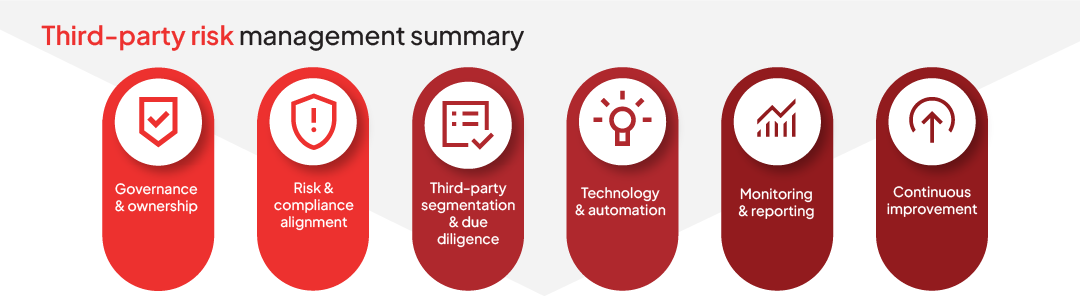
Third-party risk management is essential for protecting your organization from regulatory, operational, reputational and cybersecurity threats vendors and partners may introduce
- Leading frameworks like ISO 27001, NIST and COSO help standardize your approach, while tools like risk scoring, due diligence and continuous monitoring form the foundation of a strong program
- A TPRM maturity model can help you assess your current capabilities and plan your evolution from reactive to optimized practices
- Aligning risk and compliance teams is critical. Shared platforms, clear roles and standardized processes streamline assessments and reduce redundancy.
- AI is transforming TPRM by automating risk scoring, monitoring media and improving efficiency at scale.
- Case studies show how organizations in biotech, healthcare and manufacturing use centralization and automation to reduce onboarding time, improve oversight and strengthen compliance.
What is third-party risk management?
As you might imagine, third-party risk management — sometimes known as third-party vendor risk management — is a facet of risk management that focuses on identifying and mitigating risks relating to third parties: those risks that we have outlined above.
A third-party risk management framework aims to help organizations understand:
- Which third parties they use — often more than they think, due to incomplete data and incorrect understanding of what constitutes a third party
- How they use their third-party vendors, suppliers and partners
- What safeguards and risk management programs their third parties have in place
There are subsections of third-party risk management that relate to specific categories of risk; for instance, third-party cyber risk management, when looking at cyber risks specifically. A best-practice third-party risk management framework will encompass all of these. Terms like “third-party vendor risk management” are also often used interchangeably with third-party risk management. However, the TPRM definition can be slightly different for vendor risk management.
Third-party risk covers suppliers and business partners of all types, not simply vendors. So, third-party risk management tends to be the overarching term used to cover risk management relating to all third parties.
Increasingly, “third-party” is a reductive description, as third-party risk management today tends not just to focus on your immediate suppliers but to have fourth parties, sub-contractors and the entire supply chain in scope.
Your approach to third-party risk has to be comprehensive but proportionate. As the U.S. Government’s Office of the Comptroller of the Currency notes, your strategy should be “commensurate with the level of risk and complexity of [your] third-party relationships.”
What risks do third parties pose?
The fact that third-party risk management is so important speaks to the prevalence of third-party use. And there’s a good reason for this. Using third parties can have significant benefits:
- You can serve customers better by focusing on your core operations and outsourcing peripheral activities.
- This focus on your key strengths can also make operations more efficient and lower costs.
- Using third parties means tapping into their significant expertise; capitalizing on their experience rather than needing to build your own
- Your operations can easily be scaled up or down with customer demand.
However, third-party risk management matters because third-party vendors and partners can also pose many risks to the organizations that employ them. These risks span the spectrum of business operations. They include:
- Cybersecurity and information security risk: The risk that a third party’s actions or negligence may compromise your systems and data.
- Environmental, social and governance (ESG) risk: The risk of your suppliers failing to meet standards, whether externally mandated or set by your internal ESG policies around sustainability, social or governance matters.
- Compliance, legal and regulatory risk: The risk that suppliers, third-party vendors or business partners may jeopardize your compliance with regulations or legislation.
- Financial risk: The risk that a third party could impact your revenue. Perhaps they fail to supply to you or your customers, creating delays or putting you at risk of having to provide compensation. Perhaps they deliver a faulty component, causing costly recalls or delaying production. Maybe your revenues are impacted by association with an unethical supplier. Third-party risk management strategies are needed to tackle financial risks.
- Reputational risk: Closely related to financial risk. Many of the threats impacting your income also threaten your reputation; issues of ethics, sustainability or quality.
- Operational risk: The risk that third parties’ actions imperil your ability to operate; for instance, a supplier fails to deliver parts that your production line needs, or a third party hosting your data has an outage, impacting your systems.
- Strategic risk: Risks that strike at the heart of your corporate strategy, affecting the direction your organization wants to take.
Because the risks posed by third-party vendors and suppliers are so wide-ranging and impact fundamental areas of your business, the importance of third-party risk management has grown as an essential element of your risk management strategy.
Why is third-party risk management important?
Third-party risk is nothing new, and neither is third-party risk management. But several factors are making it more important than ever to put in place a third-party risk management program:
- Third-party risk is growing. Organizations are seeing increased issues from vendors and increased global volatility impacting customers and suppliers alike. Increasingly disruptive and increasingly frequent cyberattacks and fraud threats affect vendor reliability. As margins tighten, suppliers’ ability to absorb shocks decreases. Coupled with the trend towards outsourcing, reduced reliability in supply chains is accelerating the potential for third-party risk.
- The implications of third-party risk are becoming bigger. Regulators have supplier risk on their radar, driving businesses to focus on their supply chain risk. A growing regulatory burden relating to third-party risk is incentivizing organizations’ adoption of third-party risk management frameworks.
Third-party risk exposes your organization to threats, including:
- System and operational outages within your operations, for instance, disruption of key systems if they rely on outsourced inputs
- Interruptions to suppliers’ operations, disrupting their ability to deliver
- Issues that impact your suppliers’ integrity, ESG credentials or ability to provide you with the assurances, data or compliance that you require
Lessons from real-life third-party risk scenarios
- Your CRM system is outsourced to a third-party provider. Your ability to contact and serve customers is impacted if their system is compromised.
- A global supply chain relies on a vendor whose operations are disrupted by a typhoon. You are unable to manufacture your products as a result.
- Your supply chain due diligence uncovers that one of your suppliers is not meeting human rights standards. You need to sever links with them before they cause you reflected reputational risk.
Outsourcing is a central tenet of today’s business operations, driving efficiency and cost-effectiveness, opening up global supply chains that enable you to innovate and evolve, and allowing your company to focus on its core competencies while outsourcing non-key operations. The downside is its potential to expose your organization to supply chain vulnerabilities and threats.
An effective third-party risk management policy provides the assurance you need that you can get the most from your outsourced relationships while minimizing the risks incurred.
It is essential when considering higher-risk third parties: those who process customer data, for instance, host board or other sensitive company information or whose business continuity is crucial to your operations. Also, robust third-party risk management is a key consideration if you operate in a regulated environment.
In any of these scenarios, having a third-party risk management program in place is even more vital.
What are the goals of third-party risk management?
What is the purpose of third-party risk management? A structured third-party risk management framework can deliver significant reductions in the risks you face from third parties. From a governance point of view, it can provide data and evidence that you are taking steps to tackle the third-party risks that you face.
Putting in place an effective third-party risk management program is designed to:
- Ensure you have a comprehensive catalog of your third-party providers
- Identify the third-party risks your organization is exposed to, and prioritize these for action
- Reduce your risk of business interruption
- Minimize the regulatory, compliance, reputational and financial risks you face from third parties
- Give you a “long-range” view of incoming threats and enable you to address these future risks more efficiently and effectively
- Cut the cost of your third-party risk management activities and third-party risk mitigation
Third-party risk management best practices
Whether you are starting off on your third-party risk management journey or have already put in place the steps you need to effectively manage third-party risk, there are some best practices to follow.
What does third-party risk management best practice look like? An effective third-party risk management process will generally include the following elements:
- Identify all the suppliers who should be included in your third-party risk management program. As we noted above, this might not be confined to tier-1 suppliers. Your third-party risk management inventory should also include subcontractors and those further down your supply chain.
- Undertake supplier evaluations to assess the risk posed by each of these third parties. There are numerous ways to do this: you could issue suppliers with a questionnaire to complete about their practices and policies. This is an exercise you can carry out with existing suppliers, and should also undertake with prospective providers.
- Evaluate and segment your third-party suppliers according to the risks they pose. Categorizing your vendors and partners is an essential foundation of your third-party risk management program. This will enable you to take an appropriate and proportionate response to the risks they expose you to, based on the data obtained in your supplier evaluation exercise.
- Outline and implement a third-party risk management framework to address the risks inherent in your third-party relationships. Do you have controls to identify whether any of these risks are coming into play? What are your risk tolerances? Ensure mitigation plans are in place to quickly respond to any threats.
- Identify clear owners for all elements of your third-party risk management program. Roles and responsibilities should be unambiguous. The three lines of defense in risk management are well-established; apply this to third-party risk management to give it the structure it needs for success.
- Implement strong controls. Once organizations understand the risks they face, they should implement controls for their third parties to follow. This should all start with the contract, which can stipulate the terms of the relationship and what’s expected of the third party. But it should extend into the day-to-day of that third party’s relationship with the organization. Risk teams should also adopt continuous monitoring to ensure that all controls are correctly implemented and followed.
- Analyze the entire supply chain: Many third parties work with their vendors, suppliers and contractors, often referred to as fourth parties in third-party risk management. Organizations need to ensure that the entire supply chain is compliant. It’s best practice to include fourth parties in contracts so that they’re within the framework of the risk management strategy. This includes requiring third parties to seek approval for any fourth parties and gathering all necessary information.
- Define contingency plans for any third-party risk breaches. These will vary depending on the nature or severity of the risk in question, but need to be clearly documented and communicated so that risk mitigation plans can swing into place at maximum speed in the event of a problem.
- Create a culture of compliance from the top down: Compliance is at its best when third parties understand the importance of mitigating risk. This should start with senior management, including the C-Suite and the board. These individuals are responsible for third-party risks, so they should also take steps to cultivate third-party relationships that value compliance.
- Utilize technology: Manual risk management can only go so far. As the third-party network becomes more complex, organizations need a more efficient way to stay ahead of the risks they face. Third-party risk management solutions can help organizations manage all third parties in one place, track risk, prioritize remediation and provide real-time insights into risk.
Build a smarter TPRM program
Get a clear, actionable roadmap to building a credible, defensible, best-in-class third-party risk management program.
Examining third-party risk management frameworks
There is no single way to carry out third-party risk management; no prescribed TPRM program or framework.
There are, though, several recognized approaches that you may find useful as start points for your own third-party risk management program. Because third-party risk management can be a daunting challenge, many organizations turn to these existing frameworks to provide structure and support.
What is a third-party risk management framework?
A TPRM framework provides the structure for your third-party risk management strategy.
A framework can bring welcome clarity and guidance to the process of setting up a TPRM program. The process of putting in place third-party risk management is complex, involving multiple vendors, often spanning many countries. For each of these, you must evaluate the risks the third party brings to your organization - a process that requires exhaustive due diligence.
Third-party risk management standards to choose from
There are a number of existing TPRM frameworks. Choosing the most appropriate one will depend on the nature of your business, the types of risk you face and the resources you have available to tackle third-party risk.
Global standards and frameworks help organizations assess, control and monitor risks across their third-party ecosystem. The two most common TPRM frameworks used are the NIST third-party risk management framework, published by the National Institute of Standards and Technology (NIST), and the International Organization for Standardization (ISO).
Most frameworks can be used to supplement and bring more focus to key areas of your third-party risk management strategy. Once you’ve established your initial TPRM framework using this external guidance, you can always customize your approach or add other frameworks to prevent any gaps in risk coverage.
- ISO 27001 & ISO 27036: ISO 27001 is a globally recognized standard for information security management systems (ISMS), while ISO 27036 specifically addresses risks related to supplier relationships. Both can help risk teams protect data shared with vendors and ensure compliance with information security best practices.
- NIST SP 800-53 & NIST SP 800-161: These standards focus on federal compliance, critical infrastructure and regulated industries. While 800-53 provides security and privacy controls for federal systems and contractors, 800-161 focuses on supply chain risk management. Together, they offer detailed controls and risk assessment guidance that compliance and IT security teams can adapt to the private sector.
- COSO Enterprise Risk Management (ERM) Framework: This widely adopted ERM framework includes principles that apply to third-party oversight, encouraging integrating vendor risk into broader enterprise risk and strategic decision-making.
- ISO 37301 (Compliance management systems): This is a newer ISO standard that provides a framework for building a compliant organization, including third-party accountability. It helps compliance teams ensure that TPRM processes are defensible and auditable.
- OCC Bulletin 2013-29 (U.S. banking): A key U.S. regulatory standard, the OCC Bulletin requires banks to manage third-party relationships with the same rigor as internal operations. It sets the bar for contract oversight, risk assessments and ongoing monitoring.
- SIG and SIG Lite (Shared assessments): Organizations across sectors can uses these industry-standard third-party risk questionnaires to assess vendor controls and compliance posture. It saves time and supports scalable due diligence across high volumes of vendors.
Third-party risk management framework template
In some instances, one of the above frameworks will meet many of your TPRM needs. But in others, you may need to build or refine a third-party risk management framework that meets your unique compliance and risk objectives.
1. Governance and ownership
- Program charter: TPRM purpose, scope and guiding principles
- Roles and responsibilities: Board, executive sponsor, TPRM lead, risk, compliance, procurement, IT/security, legal
- Risk appetite statement: Thresholds for accepting, mitigating or rejecting vendor risk
- Escalation matrix: Who approves, who remediates and who reports to regulators and leadership
2. Vendor inventory
- Unique vendor ID
- Business unit and owner
- Service description and criticality
- Data and system access level (public, internal, confidential, restricted, regulated)
- Existing contracts and expiration dates
- Risk tier (Auto-populated once assessed, if using a TPRM platform)
3. Inherent risk scoping
- Geographic footprint (country, sanctions exposure)
- Regulatory touchpoints (HIPAA, GDPR, OCC, etc.)
- Cyber and operational dependency (high, medium, low)
- Potential impact categories (financial, reputational, safety, ESG)
4. Due diligence and control evaluation
- Questionnaire status (sent, received, validated)
- Document evidence (SOC 2, ISO 27001, financials, insurance certificates)
- Control gaps and findings: Map to NIST, ISO 27036 or your internal control library
- Residual risk score
- Mitigation plan and owner
5. Contracting and onboarding
- Required clauses checklist (data protection, right-to-audit, sub-processor approval, termination for breach)
- Security and privacy addendum signed? (yes/no)
- Access management actions (accounts created, least-privilege reviewed)
- Training provided (code of conduct, anti-bribery, data handling)
- Continuous monitoring feeds (financial health, cyber score, adverse media, sanctions)
- Review frequency (annual, semi-annual, real-time for critical vendors)
- Key risk indicators (KRIs): percentage of assessments overdue, number of high-risk findings open, SLA violations
- Issue/incident log: Data, description, severity, remediation status
7. Issue management and escalation
- Trigger levels (what constitutes low, medium, high severity)
- Response playbooks (data breach, financial distress, compliance violation)
- Communication plan (internal stakeholders, regulators, affected customers)
- Closure criteria and evidence
8. Offboarding and contract termination
- Data return and destruction certificate
- Access revocation checklist (applications, VPN, physical badges)
- Final risk assessment (lessons learned, recurring issues)
- Records retention period
9. Documentation, reporting and metrics
- Audit trail: System of records for assessments, approvals and evidence
- Board and executive dashboards: Top vendor risks, trend lines, remediation status
- Regulatory reporting: Mapping to OCC 2013-29, ISO 37301 or sector-specific rules
- Program KPIs: Time-to-onboard, percentage of vendors in tier one, average residual risk score, hours saved via automation
Third-party risk management regulations
A growing list of regulations pertains to third-party risk management. And while they may seem like yet another area of compliance for your business to address, they serve a valuable purpose in bringing focus to your TPRM program and, ultimately, in reducing risk.
Many regulations firmly put responsibility for third-party compliance with the company that employs them, making understanding and complying with third-party risk management regulations a necessity rather than a nice-to-do.
Third-party risk management regulations have a number of benefits to suppliers and users alike:
- Third parties are held accountable and, as a result, operate to higher standards
- Identifying compliant, ethical — and therefore hopefully lower-risk — suppliers is easier
- Due diligence of new suppliers is, therefore, simpler and quicker
- Reduced risk of business interruption and disruption
- Regulatory requirements bring structure to the third-party risk management lifecycle with inbuilt controls and metrics
- In combination with the frameworks we’ve noted above, third-party risk management regulations create consistency and make best practices visible and actionable
The same third-party risk management regulations that will apply to your organization will depend on your location and the jurisdictions in which you operate.
Well-known third-party risk management regulations
Some of the best-known third-party risk management regulations include:
- GDPR — the General Data Protection Regulation. A European Union (EU) regulation, the GDPR applies to any organization processing data on EU residents, no matter where the organization is located. Non-compliance brings significant financial penalties.
- Sarbanes-Oxley Act (SOX) — SOX applies to all U.S public companies. Its requirements are aimed at ensuring financial statements and disclosures are accurate and reliable.
- HIPAA — the Health Insurance Portability and Accountability Act of 1996. HIPAA is another data protection regulation applicable to the healthcare sector. It sets rules for healthcare providers and third parties around the maintenance, use, sharing and protection of personally identifiable information.
Third-party risk management maturity model
Organizations vary widely in how they manage third-party risk, from basic vendor tracking to fully integrated, enterprise-wide programs. A maturity model helps you evaluate where your organization stands and what capabilities you need to evolve.
Below is a five-level model outlining typical stages of TPRM maturity, with guidance for both compliance and risk functions at every level.
| Level | Risk management | Compliance | Tools | Next steps |
| 1: Foundational | Vendor risk is assessed inconsistently or only after issues arise. No formal risk scoring or visibility into the full vendor base. | No documented policies or audit-ready procedures. Regulatory obligations may be unmet or reactive. | Manual tracking via email and spreadsheets. No centralized system. | Create a vendor inventory and establish basic due diligence procedures. |
| 2: Reactive | Some inherent risk assesments performed pre-contract, but not standardized. High-risk vendors may receive more attention, but others are overlooked. | Policies may exist, but are inconsistently applied. Regulatory gaps still present. | Document templates and shared folders begin to replace ad hoc tracking, but still mostly manual. | Formalize workflows and begin segmenting vendors by risk tier. |
| 3: Defined | A structured TPRM process is in place with tiered risk reviews, due diligence and periodic reassessments. | Auditable processes, documented policies and regular training exist. Able to support most regulatory requirements. | Use of purpose-built risk management tools or lightweight GRC platforms. | Introduce automation, performance monitoring and cross-functional coordination. |
| 4: Integrated | Risk scoring, real-time monitoring and integrated workflows enable proactive identification and escalation of issues. | Embedded into procurement and contracting. Aligned with enterprise risk management and regulatory updates. | Centralized platforms with automated workflows, dashboards and third-party data integrations. | Expand to include ESG risk, fourth-party oversight and board-level reporting. |
| 5: Optimized | TPRM is embedded into business strategy and decision-making. Continuous improvement is driven by analytics and threat intelligence. | Supports a defensible position across audits, investigations and certifications. Real-time adaptability to regulatory changes. | Fully integrated enterprise systems, predictive analytics and AI-driven insights. | Sustain momentum through governance reviews, stakeholder engagement and ongoing innovation. |
How compliance and risk teams can streamline TPRM efforts
Effective third-party risk management is multi-faceted, depending on strong policies, tools and alignment between the teams who implement them. Risk and compliance functions have overlapping and easily siloed responsibilities. Without clear coordination, this can lead to duplicated efforts, missed risks or vendor bottlenecks.
Here’s how these teams can work better together to build a more scalable and defensible TPRM program.
- Clarify roles and shared ownership: Define who owns which parts of the vendor lifecycle and where collaboration is critical. Compliance teams will typically lead on regulatory requirements, documentation and policy enforcement, while risk teams tend to own assessments, scoring models and continuous monitoring. Both teams will collaborate on due diligence, escalation and board reporting.
- Align on risk appetite and thresholds: When teams define risk severity differently, vendors can get stuck in unnecessary reviews or be approved without sufficient scrutiny. Use joint working sessions to agree on what “high risk” means and when a risk requires escalation.
- Standardize due diligence and monitoring protocols: Avoid redundant or inconsistent questionnaires by building a shared control library and standardized templates. Start by aligning on which frameworks you’re evaluating against, then use automation to distribute questionnaires and send reminders. Then, divvy up monitoring responsibilities. Risk can handle cyber and financial feeds, while compliance tracks regulatory developments.
- Streamline reporting and escalation: Collaborate on dashboards and risk reports that meet both operational and regulatory needs. Create reporting tiers, one for compliance metrics and another for risk exposure. Establish escalation workflows with clear criteria, approvers and documentation steps.
- Meet regularly and review the program jointly: Schedule quarterly meetings between risk and compliance to review vendor trends, audit findings and process bottlenecks. Cross-functional reviews help surface and resolve recurring issues, align on upcoming regulatory changes and identify where automation or process changes could improve efficiency.
- Adopt a shared platform: Centralize vendor data, assessments, documents and approvals in one system, not across spreadsheets and inboxes. A shared TPRM platform ensures consistent data entry and workflows, visibility across teams and version control and audit readiness.
Third-party risk, simplified
Get comprehensive guidance on how to elect the right third-party risk management software directly from compliance expert and former CCO Kristy-Grant Hart.
Third-party risk management process: Core elements and lifecycle steps
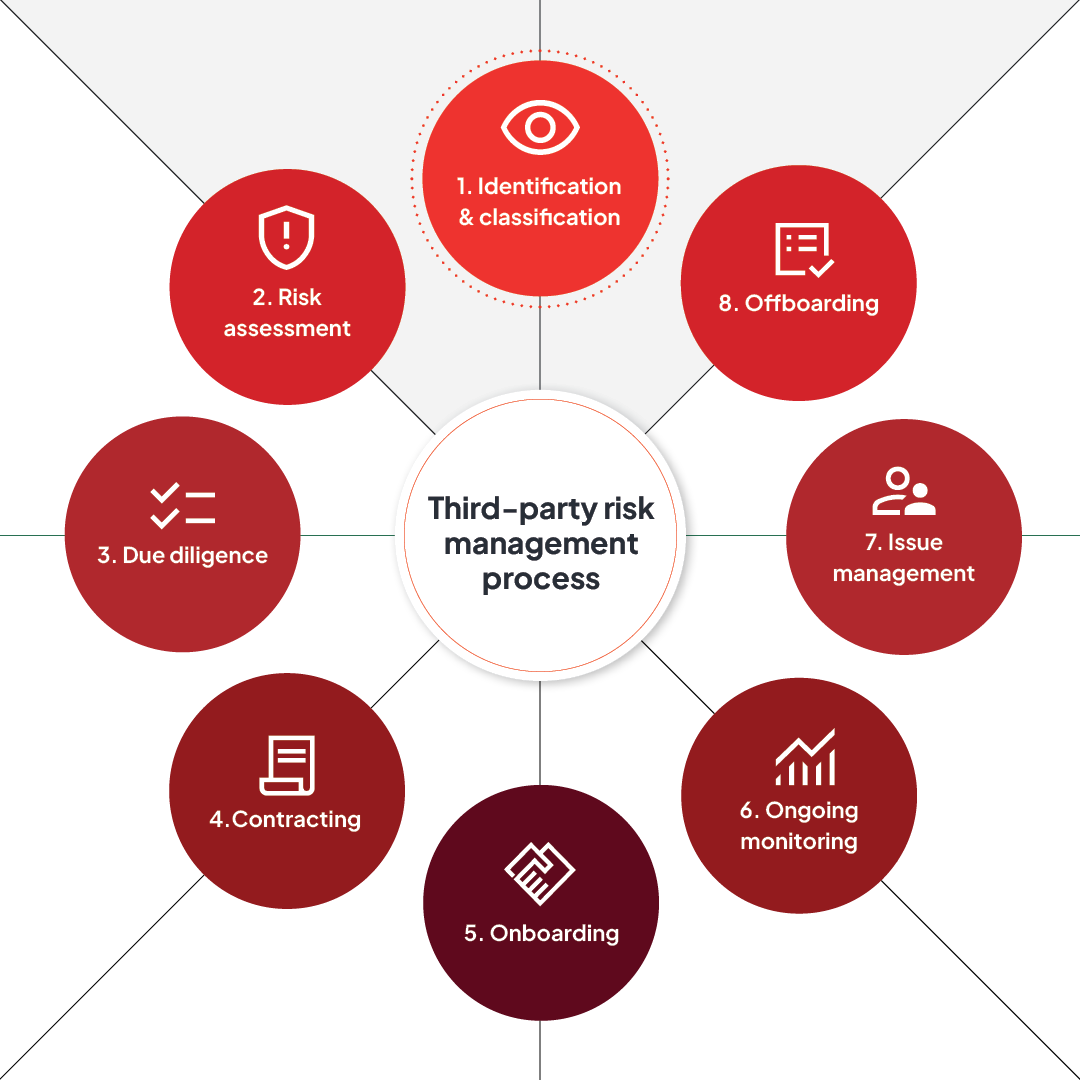
A strong TPRM program requires both a solid foundation and a well-defined third-party risk management process — one that promotes regulatory compliance while managing operational and reputational risks proactively. Compliance, procurement, security and risk teams must collaborate closely to achieve these goals.
Key elements of third-party risk management
These are the foundational components that TPRM teams rely on to manage third-party exposure:
- Governance and policy framework: This framework establishes clear ownership, cross-functional roles and documented policies to guide how teams identify, assess and mitigate third-party risks. In other words, who owns TPRM risk and how will they manage it?
- Risk tiering and classification: Different vendors need distinct risk management approaches. Segmenting vendors based on the type of service, access to sensitive systems and data and potential business impact can focus your TPRM efforts.
- Due diligence and risk assessment tools: Standardized questionnaires, document reviews and third-party intelligence feeds are essential to evaluating a vendor’s cybersecurity posture, financial stability and compliance history.
- Contractual safeguards: This includes contract clauses for data protection, right to audit, service level expectations, incident response and termination rights.
- Ongoing monitoring and performance management: Track vendor risk post-contract using tools like third-party risk management platforms, reassessment schedules and key performance indicators (KPIs).
- Issue management and escalation protocols: A centralized process for logging, prioritizing and resolving vendor related incidents and compliance issues breaks silos between risk and compliance teams and gives both holisitc insights.
- Auditability and reporting: Documentation and dashboards are critical to defending your TPRM program through audits, board reporting and internal accountability.
Step-by-step third-party risk management workflow
These are the key TPRM workflows that bring the above elements to life across the entire third-party lifecycle.
- Third-party identification and inventory: Build and maintain a centralized inventory of all vendors. Your risk tiering and classification will support this process, as your inventory should include services provided, criticality and risk tiers.
- Inherent risk scoping: Assess the risk posed by each vendor before you apply controls. Consider geography, regulatory exposure and access to systems and data.
- Due diligence and evaluation: Risk and compliance teams should collaborate to collect documents, assess controls and perform risk reviews. You can use internal tools and external data sources to ensure that no stone goes unturned and that you can store the data you collect securely.
- Approval and contracting: Based on what you’ve uncovered, decide whether to engage the vendor. Finalize contracts using any of the above contractual safeguards to build in risk mitigation language.
- Secure onboarding: Configure access controls, provide training if needed and communicate compliance expectations. Only give third parties the exact access level they need to fulfill their obligations; no more and no less.
- Ongoing monitoring and reassessment: Continuously monitor vendor performance, compliance and emerging risks through reassessments and performance reviews. Be prepared to execute issue management and escalation protocols as needed, whether for risk or compliance challenges.
- Issue resolution and incident management: Escalate and address vendor issues quickly to contain impact and meet legal obligations.
- Offboarding and contract termination: Securely disengage vendors when relationships end. Revoke access, retrieve data and document the process.
How to implement third-party risk management
Policies and checklists are the start of most third-party risk management programs. However, the most effective programs build cross-functional alignment, choose the right tools and operationalize a scalabe process. Both risk and compliance play key roles in each phase.
Below are the core steps to implement a TPRM program that meets regulatory expectations and mitigates real-world risk.
- Establish governance and cross-functional ownership: Implementation is strongest with clear ownership and collaboration between key teams. Compliance is responsible for regulatory alignment, policy development and audit readiness. Risk management, on the other hand, will oversee vendor risk scoring, control evaluation and residual risk decision-making. The work of both teams will feed into how procurement, legal and IT/security manage the third party.
- Define scope and risk appetite: Identify which third parties fall within the program’s scope. This could be vendors with access to sensitive data or systems, critical service providers or contracts or partners in regulated jurisdictions or industries. You can then collaborate with leadership and the board to set a risk appetite, which will determine which risks to accept and which to mitigate or reject.
- Develop TPRM policies, standards and procedures: Document and formalize the program. TPRM policies outline the program’s purpose, scope and governance, while standards and procedures offer step-by-step instructions for onboarding, due diligence, reassessments and offboarding. All procedures should align with regulatory requirements like OCC guidelines, GDPR or industry-specific frameworks.
- Choose and configure the right technology: Look for tools that help automate and scale your program. Consider platforms that centralize vendor inventory and classification, automate risk assessments and workflows, offer real-time third-party intelligence feeds and unify reporting dashboards to fuel compliance audits and board-level visibility.
- Establish and automate workflows: Using your TPRM solution, design clear, role-based workflows to support a consistent and auditable process. The best technology should support automating various tasks, like approval routing based on vendor risk tier, due diligence questionnaire distribution and tracking, risk scoring and escalation triggers, review and reassessment notifications and issue resolution and documentation tasks.
- Pilot the program with a subset of vendors: Before a full rollout, select a representative sample of third parties across risk tiers and business functions. Run the full TPRM process, from risk scoping, due diligence and contracting to onboarding and monitoring. Track time, bottlenecks and gaps across functions.
- Train stakeholders across the business: Educate business units, vendor owners and procurement staff on how to uphold TPRM. Training should touch on their role in the TPRM process, when and how to escalate vendor risks and what information to collect and maintain. Compliance teams can own training on regulatory obligations, while risk teams should lead sessions on identifying red flags.
- Scale, optimize and continuously improve: After the pilot, expand to all in-scope vendors. Introduce tier-based oversight models, where high-risk vendors are reviewed more frequently. Monitor program KPIs like risk reduction over time, SLA compliance and relevant vendor issues.
- Document and report TPRM activities: A mature TPRM program depends on well-maintained documentation and transparent reporting. You should maintain up-to-date policies, procedures and workflows to demonstrate program integrity and consistency. Archive all vendor-specific documentation, like risk assessments and due diligence materials. Doing so will give compliance teams acess to time-stamped audit trails, signed approvals and control evidence for regulatory reviews.
How to manage third-party risk
Once your third-party risk management framework is in place, the real challenge begins: actively managing vendor risks day-to-day. This involves following the process but also adapting based on practical strategies, real-time insights and cross-functional coordination.
Here are proven ways to manage third-party risks effectively, with real-world examples from organizations that have done it well.
1. Automate vendor risk assessments to save time and increase coverage
Eliminating manual processes like spreadsheets and email surveys is critical. You’ll never miss a vendor assessment, key risk score or compliance follow-ups, which is especially impactful in high-volume and highly regulated industries like healthcare.
Consider a major healthcare provider facing persistent delays in its third-party risk management program. Limited staff and manual worfklows — email requests, spreadsheets and ad hoc surveys — meant it could only asses a small selection of vendors each year, creating compliance blind spots.
By implementing an automated platform, the organization:
- Streamlined data gathering and risk scoring
- Integrated third-party intelligence with existing workflows
- Automated notifications, escalations and risk memos
Ultimately, automation helped the vendor increase vendor assessments by 373% in its first year using the new platform, save 1,300 hours for 200 vendor reviews and flag and escalate high-risk vendors faster.
2. Accelerate third-party onboarding without sacrificing due diligence
Streamline onboarding by automating follow-ups, benchmarking performance and tightening due diligence procedures so risk reviews don’t stall business growth.
One organization found that manual due diligence drug out third-party onboarding to nearly three times the desired timeline, directly impacting business agility and delaying key partnerships.
They implemented Diligent Third Party Risk Management - Compliance, which:
- Sent task reminders and biweekly stakeholder progress reports to maintain accountability
- Introduced benchmarking against industry standards to identify inefficiencies
- Restructured onboarding procedures for clarity and speed
These changes ultimately reduced onboarding time by 25%, due diligence processing time by 50% and enabled a faster time-to-contract. Automating accountability and aligning your process with best practices helps balance speed and risk control.
3. Simplify compliance through tiered risk management and training
Compliance outcomes are stronger and more predictable when you streamline third-party due diligence, automate workflows and deliver targeted, multilingual training to build employee buy-in.
Victaulic, for example, rapidly modernized its third-party compliance program by adopting a centralized platform that replaced manual processes and improved global consistency.
The company implemented:
- Tiered due diligence with risk-based categorization that streamlined assessments and helped tailor oversight to vendor risk levels
- Centralized compliance data — distributor records, training logs and investigations — within one unified TPRM platform, improving access and audit readiness.
- Automated workflows that freed up compliance staff to focus on more strategic initiatives.
- Custom training delivery, including multilingual options and microlearning styles increased completion rates and made compliance education more engaging
- Proactive brand protection by automating media monitoring, which flagged potential risks early and reinforced Victaulic’s strong compliance reputation.
Strengthen your compliance approach
Gain expert guidance to implement effective, scalable processes for stronger third-party compliance and risk management.
4. Centralize and automate to scale with limited resources
A centralized, automated TPRM platform improves visibility, reduces false positives and helps lean teams stay compliant without sacrificing oversight.
For example, a global biotech manufacturer faced serious compliance and resource constraints after a $50 million FCAP enforcement action and significant reductions to its compliance team. Their existing risk tools produced poor-quality reports and frequent false positives, undermining trust in the program.
The organization implemented Diligent Third Party Risk Management for its:
- High-quality investigative reporting from seasoned analysts
- Real-time proprietary risk intelligence
- Automated onboarding and monitoring workflows
- Seamless integration with key systems
As a result, the biotech company enhanced its compliance, strengthened its data privacy practices and improved efficiency even with fewer staff. The centralized approach also improved accountability, adjusted easily to regulatory changes and brought clarity to the entire TPRM lifecycle.
How to address common TRPM issues
Third-party risk management is an essential element of today’s risk management strategy. But it’s not without its challenges. Common TPRM stumbling blocks include:
- Onboarding and inventory. Onboarding and creating a centralized repository of third-party suppliers can be labor-intensive and time-consuming. Standardized or best practice controls should be included as standard. A document register will enable you to get a full picture at a glance. Automating the process can be transformative.
- Third parties can be outside your risk management process. You must put in place a Corrective Action Plan (CAP) for any risks you identify; a plan that automatically recommends, approves and applies remediation actions. If your third-party partners are not part of this plan or the solution that supports it, you will not succeed in managing their risks.
- Risks are not routinely and accurately assessed or prioritized. Automate your process for classifying, assessing and tackling the risks your third parties pose, and you will bolster your approach as well as reduce inefficiency and duplication.
- Many organizations use an identical data-gathering process for all of their third parties. This can be unnecessary and over-engineered, wasting time and money and drowning staff in paperwork. Focus your data-gathering on identifying high-risk suppliers and drilling into those rather than subjecting all third parties to the same onerous, “one size” third-party risk management approach.
- Monitoring is ad-hoc with no schedule or structure. Third-party risk management should be a continuous process, with data gathering tailored to the risk profile of the third party. Automating this process can pick up changes to risk level, allowing you to flex your approach as needed.
- Reporting is unclear or incomplete. As mentioned above, data-overwhelm helps nobody. You need out-the-box dashboards and customizable tools to enable meaningful, concise and relevant reporting. A solution that grows with you will allow your third-party risk management framework to evolve with your changing needs.
- Future-proofing your third-party risk management program can be difficult. With regulatory requirements, corporate ambitions and consumer expectations constantly shifting, a flexible approach to third-party risk management is key. As Fola Ojumu, Partner, Kearney & Company, noted at Diligent’s Modern Governance Summit 2022, “You need an adaptive strategy to react to change — otherwise you miss emerging risk.” A rigid TPRM solution can stifle your ability to change as needed. Third-party risk management best practices include adapting your approach to the external landscape, and the route you choose must accommodate this.
As with any risk management challenge, a structure around your approach is essential. In the same way that you might create a checklist for your wider audits and assessments, it helps to take a systematic stance on TPRM. Fortunately, there are third-party risk management solutions that can help you.
AI third-party risk management
AI is rapidly becoming a core third-party risk management capability. Organizations are turning to AI not only for efficiency but also to keep up with more complex ecosystems and growing regulatory pressure. When the question is how to scale due diligence, identify risks faster and reduce manual workloads, AI has become the clear answer.
For both risk teams, who need earlier visibility into vendor threats, and compliance teams, who require defensible documentation and real-time monitoring, AI-driven solutions offer practical ways to modernize and strengthen TPRM programs.
Both risk and compliance teams are beginning to leverage AI to improve decision-making, reduce human workload and flag risks earlier in the vendor lifecycle. Here’s how AI is transforming core aspects of TPRM:
- Automated risk scoring: AI can analyze structured and unstructured data — vendor questionnaires, financial filings, news coverage and more — to generate dynamic risk scores. These scores evolve in real time as new information becomes available. This capability gives risk teams faster prioritization of high-risk vendors, while compliance teams gain audit-ready scoring logic tied to clear inputs.
- Adverse media and ESG monitoring: Instead of manually scanning the news, AI models can continuously crawl and classify global media, flagging stories related to fraud, sanctions, labor violations or ESG controversies tied to your third parties. This means compliance teams will receive earlier alerts, and risk teams can initiate mitigation or escalation before reputational damage occurs.
- Smart due diligence reviews: AI can help summarize vendor responses to questionnaires, flag inconsistencies and detect evasive language. AI can also suggest follow-up questions based on historical issues or known risk patterns. These features reduce time spent reviewing lengthy responses, especially with high volumes of vendors.
- Predictive risk modeling: AI can identify patterns that precede risk events — financial distress, delivery delays or cybersecurity vulnerabilities — by analyzing historical vendor data, peer comparisons or external intelligence feeds. This empowers risk teams to act before issues occur, rather than after they escalate.
- Intuitive TPRM workflows: AI-powered automations streamline onboarding, compliance processes, renewals and continuous monitoring of third-party relationships. Compliance and risk teams alike can leverage these workflows to ensure no stone goes unturned — and no risk goes unflagged.
Benefits of third-party risk management software
The right third-party risk management solution can transform your ability to tackle your TPRM challenges:
- Automating the process makes it more robust, from data gathering, through risk scoring and analysis, to remediation.
- Third-party intelligence can be integrated into your approach to deliver a 360-degree (and up-to-the-minute) vision of third-party risk at all times.
- Existing workflow processes and legacy data can be easily integrated.
- Third parties’ risk profiles are evaluated to prevent over-engineering.
- Risks can be accurately assessed and prioritized for action, reducing unnecessary work, duplication and wasted resources.
- Reporting is clear, customizable and appropriate for your stakeholders, providing clear snapshots of progress.
- A more efficient process enables you to fast-track TPRM, increasing risk assessments, bolstering data gathering and controls, and accelerating remediation.
- The best solutions will future-proof your third-party risk management strategy, allowing you to optimize your TPRM process at every stage.
Boost TPRM with technology
See all the ways you can protect yourself with our complete roadmap to IT and third-party risk management technology.
Simplify and scale your TPRM program with Diligent
Third-party risk management is a strategic capability that depends on strong collaboration between risk and compliance teams. Yet, programs stall all too often due to inefficient manual processes, fragmented data and tools that can’t scale.
Diligent Third Party Risk Management, part of the Diligent One Platform, bridges the gap. With centralized workflows, automated assessments, real-time monitoring and built-in reporting. Diligent empowers both risk and compliance teams to work from a shared source of truth — reducing blind spots, improving oversight and accelerating decisions.
Request a demo to see how Diligent Third-Party Risk Management can help your organization simplify third-party risk management, strengthen your regulatory posture and build a program that grows with you.
Third-party risk management FAQs
How do I assess the current maturity level of my third-party risk management (TPRM) program?
Assessment typically involves evaluating your program against recognized maturity models. Key areas to consider include: governance structure, policy completeness, risk identification and segmentation practices, integration with business processes, technology utilization, due diligence rigor, continuous monitoring, and incident response protocols. Tools such as self-assessment questionnaires, gap analyses or external audits can benchmark your maturity. Diligent’s resources and platform also provide frameworks for maturity assessment.
As a data owner relying on third parties, how do I minimize my liability in case of a data breach?
To minimize your liability from a data breach, institute rigorous due diligence on vendor security, mandate contractual liability and notification clauses, require cyber insurance, conduct regular security reviews and document compliance. Shift risk where possible via indemnification but maintain active oversight and response planning.
What are the key workflows and automation options for streamlining third-party onboarding and renewals?
Critical workflows include risk segmentation questionnaires, automated document collection (e.g., insurance, certifications), workflow-triggered due diligence, digital signature integration and automated reminders for renewals or reassessments. Automation reduces errors, accelerates onboarding and documents every step for auditability.
How do I ensure our TPRM program addresses global regulations such as GDPR and other data privacy laws?
Ensure data mapping and flow visibility, conduct privacy impact assessments, require contractual data privacy clauses and verify vendor compliance certifications (e.g., ISO 27701). Ongoing due diligence should assess vendors’ privacy policies and incident response plans, while Diligent facilitates centralized documentation for regulatory proofs.
What are the latest regulatory trends impacting third-party oversight in 2025, especially for AI, supply chain, and cybersecurity?
Key trends include: stricter supply chain transparency (e.g., EU CSDDD), new AI-specific risk regulations (EU AI Act), updated cyber risk disclosure rules (e.g., SEC, DORA in Europe), increased ESG reporting mandates and renewed focus on critical vendor resilience following major geopolitical events.
What are the best practices for using in-depth analytics to get a consolidated view of risk across my organization?
Integrate disparate risk data, ensure taxonomy consistency, leverage dashboards and heatmaps and automate aggregation of risk indicators. Apply filters for sector/region/function. Diligent’s analytics suite provides customizable views to identify systemic vulnerabilities and inform board-level reporting.
What steps can I take to move from a manual or spreadsheet-based TPRM approach to an automated, scalable solution?
Steps include: mapping current workflows, identifying manual pain points, articulating key system requirements, soliciting cross-functional stakeholder input, selecting a TPRM platform supporting automation and prioritizing integrations (e.g., with procurement or GRC systems). Phased rollouts, data migration planning and user training support adoption. Diligent’s platform can transition teams from reactive to proactive TPRM via workflow automation and risk scoring.
How can I use AI-driven monitoring systems to improve ongoing due diligence and risk detection?
AI-enabled tools facilitate continuous monitoring by analyzing large volumes of unstructured data (e.g., news, sanctions updates, social media) for early risk indicators. Proactive alerts allow teams to intervene before risks materialize. Diligent’s solutions offer automated monitoring for adverse media, compliance violations and ESG risks.
What is the best budget-friendly third-party risk management software?
The best budget-friendly third-party risk management software depends on your organization’s size, regulatory requirements, risk profile and existing tech stack. Some tools focus on automating due diligence or monitoring, while others offer broader capabilities like workflow management, document tracking or real-time alerts.
Our Third-Party Risk Management Software Buyer’s Guide will give you the exact criteria to consider as you compare features and your own implementation needs so you find the right fit without overspending. Download the guide to get started.
What tools are available to continuously assess third-party cyber risk posture?
Use platforms providing external threat intelligence, vulnerability scoring, security rating services and integration with SIEM/SOC alerts. Diligent offers automated cyber risk monitoring, configurable alerts, and vendor self-assessment modules.
How can I demonstrate ROI or tangible outcomes from investing in TPRM solutions?
Track and report metrics: reduction in risk incidents, audit and compliance pass rates, operational cost/time savings, shortened onboarding, and improved contract and risk visibility. Leverage case studies (from Diligent and sector peers) in quantifying such impacts.
Numerous organizations report significant improvements: one global financial firm streamlined vendor assessments and cut onboarding time by 40%; a manufacturing multinational achieved full audit readiness in weeks, not months, after deploying Diligent. Additional case studies can be provided by Diligent on request.
Third-party risk management resources
Topic: Automation
Who is it for: Compliance teams, risk teams
Resource type: Blog
Summary: Third-party risk is ever-growing. Learn how to put your TPRM program on autopilot in five simple steps.
Link: How to automate third-party risk management
----------------------------------------------
Topic: Prioritization
Who is it for: Compliance teams, risk teams, board of directors
Resource type: Podcast
Summary: Keeping up and remaining compliant is more challenging than ever. Discover how to approach the board about making third-party risk management a priority.
Link: Reprioritizing third-party risk management
----------------------------------------------
Topic: Metrics
Who is it for: Compliance teams, risk teams
Resource type: Blog
Summary: Third-party risk management metrics help you understand whether your strategy is working. Learn how to select metrics meaningful to risk, compliance and the board alike.
Link: Third-party risk management metrics
----------------------------------------------
Topic: Training
Who is it for: Compliance teams, risk teams
Resource type: Tools, templates and videos
Summary: Building a culture of compliance embeds third-party risk management principles enterprise-wide. Diligent Compliance and Ethics Training offers powerful, behavior science-based tools to grab employees’ attention and make compliance the standard.
Link: Compliance and ethics training
----------------------------------------------
Topic: Technology
Who is it for: Compliance teams, risk teams
Resource type: Guide
Summary: Technology powers more comprehensive third-party risk management. Explore how your organization can use software to enhance your strategy.
Link: Technology and risk management


