
For general counsels and chief risk officers at large organizations, enterprise vendor risk management (VRM) sits squarely on the board agenda. Your organization likely depends on hundreds or thousands of third parties for critical services — and each one represents potential exposure to cybersecurity breaches, operational failures and regulatory violations that land on your desk.
According to the 2026 What Directors Think report by Diligent Institute and Corporate Board Member, 84% of boards have changed their scenario planning approach in the past five years due to heightened risk, with 45% now incorporating supply chain disruptions into their crisis preparedness exercises.
Yet only 6% of directors cite strengthening third-party and supply chain risk oversight as a top 2026 priority, revealing a gap between recognized exposure and dedicated governance attention.
Regulators have noticed. Frameworks like digital operational resilience act (DORA) in the EU, APRA CPS 230 in Australia and the UK FCA's Critical Third Parties regime — all effective in 2025 — now require documented vendor oversight with structured processes, continuous monitoring and direct board accountability. The days of informal vendor management are over.
You already know third parties create exposure. The hard part is building governance infrastructure that satisfies regulators while actually reducing real risk — not just checking compliance boxes.
To this end, we’ll cover:
Enterprise vendor risk management is the systematic identification, assessment, mitigation and monitoring of risks across your entire third-party ecosystem — from strategic partners and technology providers to outsourced service providers and supply chain vendors.
VRM ensures that the use of service providers does not create unacceptable potential for business disruption or negative impact on business performance. This strategic focus differs from traditional vendor management, which emphasizes controlling costs and negotiating contracts.
The key distinction: You remain fully accountable for third-party performance as if the activity were conducted internally. Using third parties does not diminish your board's and senior management's responsibility for safe and sound operations. This retained responsibility doctrine is why vendor risk management belongs on the governance agenda, not just in procurement.
The business case for elevated vendor risk governance is compelling. Supply chain and third‑party vendor compromise breaches cost organizations an average of USD 4.91 million — higher than the global average breach cost according to IBM's Cost of a Data Breach Report. These elevated costs reflect complexity in identifying compromise points across multi-tier vendor relationships and contractual limitations in accessing vendor security logs during investigations.
Yet supply chain accountability ranks among the most underestimated compliance risks according to the 2026 What Directors Think report, with only 15% of directors recognizing the gap — even as 26% expect cross-border trade, export controls and sanctions compliance to demand significant board attention this year. The disconnect highlights how third-party exposure often flies under the radar until a compliance failure surfaces.
Organizations without safeguards — especially those with cross-border interests in politically sensitive industries — face heightened risk. Regular top-down reviews help assess risk tolerance and preparedness for escalating tensions.
An effective enterprise VRM program rests on five pillars:
Start with a complete vendor inventory from procurement, accounts payable and IT systems, capturing services provided, data access levels and operational criticality.
Apply specific criteria to identify critical vendors: access to customer personal data or financial information, services affecting revenue-generating operations, regulatory compliance dependencies or no viable alternative vendor within 90 days.
Implement a tiered classification system:
Document your risk tiering methodology in writing and obtain board approval. This ensures your classification captures the full risk profile of each vendor relationship and enables proportionate oversight.
Boards hold ultimate responsibility for approving third-party risk management policies and risk appetite, receiving regular reporting on significant risks and incidents, ensuring adequate program resources and holding management accountable for effectiveness.
You need to define accountability across functions. For example:
"There needs to be collaboration between risk and the business, vertically up and down, but then also horizontally across the organization," says Michael Rasmussen, CEO of GRC Report. "The problem is there are silos."
Structure your program around the lifecycle stages regulators expect: planning, due diligence, contract negotiation, onboarding, ongoing monitoring and termination. Each stage builds on the previous one, creating a continuous cycle of risk management rather than isolated checkpoints.
Pre-contract due diligence should be proportionate to vendor criticality. Screen against OFAC, EU and UN sanctions lists, verify financial stability with audited financial statements and confirm beneficial ownership structures.
For critical vendors, require independent security validation — SOC 2 Type II reports, ISO 27001 certifications, recent penetration testing results and documented incident response capabilities. Relying on vendor self-assessments alone is like accepting management assertions without independent audit verification.
Monitoring frequency should match risk tiers. Critical vendors need continuous automated monitoring with quarterly reassessments. High-risk vendors require semi-annual reviews, medium-risk annual and low-risk biennial.
But schedules alone aren't enough — supplement with event-driven triggers. Material scope changes, security incidents, M&A activity or financial distress should prompt immediate reassessment regardless of where you are in the cycle.
Structured offboarding should begin 90-180 days before termination. Revoke all access comprehensively, ensure data return in usable formats and obtain written certification of data deletion within 30 days. Poor exits create lingering risk, so treat offboarding with the same rigor as onboarding.
Document risk appetite statements defining acceptable vendor risk levels — zero tolerance for critical vendors without SOC 2 Type II certification, maximum concentration limits for critical services and minimum control maturity levels for data processors.
Additionally, position vendor risk within your broader enterprise risk management framework rather than maintaining it as an isolated program. Continuous monitoring findings should feed into enterprise risk registers, executive dashboards and strategic planning processes.
Third-party breach involvement has escalated dramatically. This makes contractual protections your primary legal defense when vendor failures occur.
Manual vendor risk processes struggle to keep pace with the scale and velocity of enterprise third-party ecosystems. Spreadsheet-based vendor tracking, email-driven assessments and document-based compliance reporting leave gaps that compromise oversight — often discovered only during audits or regulatory examinations.
"Risks are all integrated; they're not isolated," says Edna Conway, Board Director and Executive Advisor. "Where can I go to get that information a) swiftly, b) in a palatable, absorbable way? That's what we're looking for."
Purpose-built governance platforms eliminate this fragmentation, transforming reactive vendor compliance into proactive risk management.
The Diligent One Platform unifies governance, risk and compliance functions into a single connected infrastructure — reducing the silos that allow vendor risk gaps to go undetected. Within the platform, multiple solutions directly address the challenges that undermine third-party oversight quality.
Third-Party Risk Manager delivers comprehensive vendor lifecycle management from onboarding through continuous monitoring:
For organizations with technology-heavy vendor portfolios, IT Vendor Risk Management provides specialized capabilities for IT and cybersecurity risk:
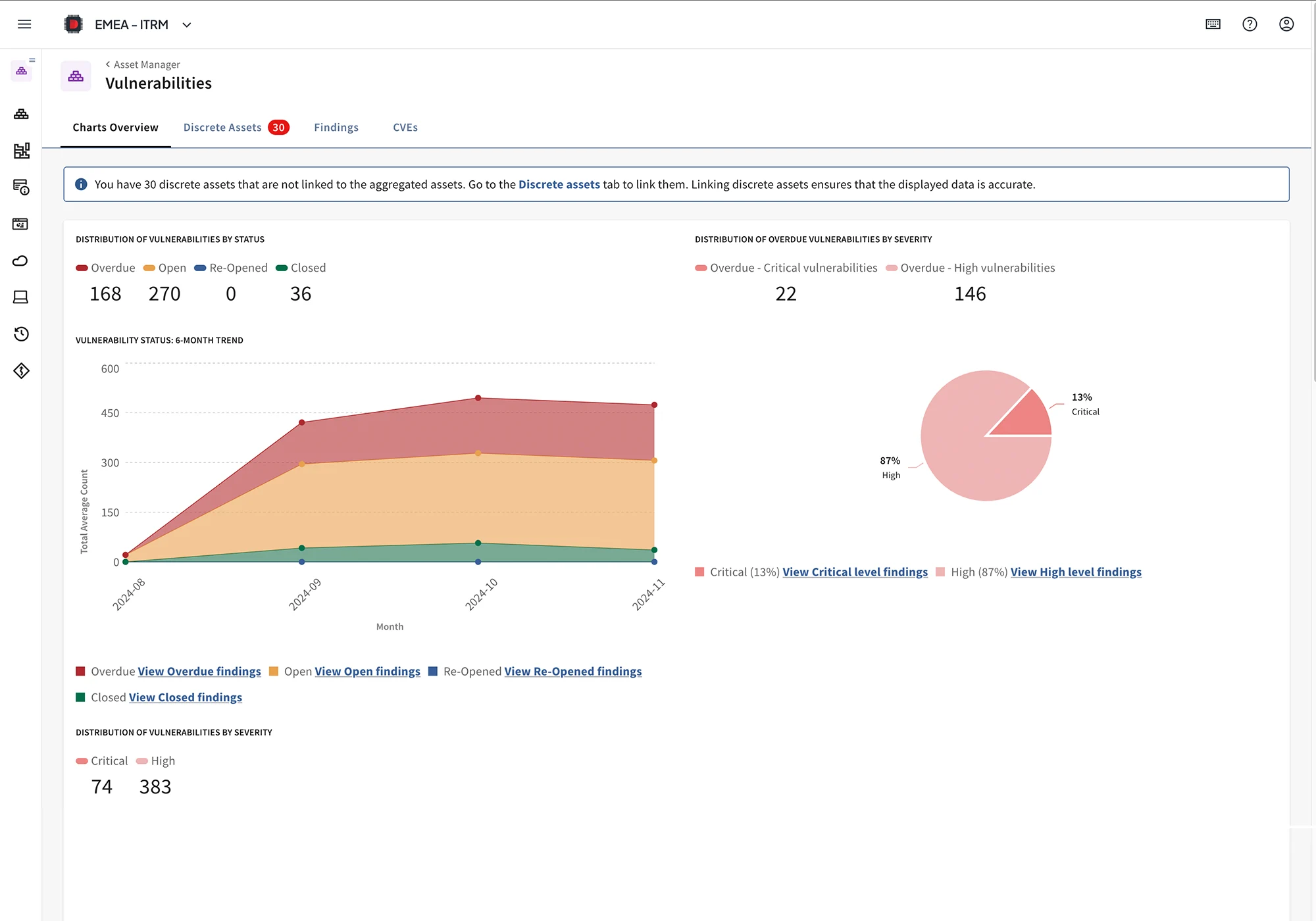
These integrated capabilities ensure that vendor risk management moves from policy documents to operational reality — providing the accountability, transparency and oversight that regulators and stakeholders increasingly demand.
Whether you're establishing your first formal third-party risk management program, preparing for DORA compliance or demonstrating vendor oversight maturity to investors, integrated governance technology provides the accuracy and efficiency that manual processes cannot match.
Book a demo to see how Diligent helps organizations transform vendor risk from fragmented oversight into unified, board-ready capability.
Third-party risk involves the vendors and service providers your organization contracts with directly. On the other hand, fourth-party risk extends to your vendors' vendors — the subcontractors, cloud providers and service companies that your direct vendors rely upon.
Assessment frequency should align with vendor risk classification:
Beyond scheduled assessments, event-driven triggers like security incidents, M&A activity or material scope changes should prompt immediate reassessment regardless of the standard schedule.
Board reports should answer four questions: Which critical vendors underwent assessment this quarter? Which vendors exceeded risk thresholds requiring remediation? What percentage of vendors meet baseline security standards? Where are we vulnerable if a vendor fails tomorrow?
Present 5-7 key metrics with traffic light indicators, lead with business impact rather than technical scores and include both leading indicators (concentration risk, assessment coverage) and lagging indicators (incidents, breaches, disruptions).
Ready to build board-ready vendor risk management that satisfies regulators while reducing real risk? Schedule a demo to discover how Diligent delivers unified third-party oversight.